What types of encryption are there?
In more detail
- What types of encryption are there?
- What is symmetric encryption?
- What is asymmetric encryption?
- What about hashing?
What types of encryption are there?
There are two types of encryption in widespread use today: symmetric and asymmetric encryption. The name derives from whether or not the same key is used for encryption and decryption.
What is symmetric encryption?
In symmetric encryption the same key is used for encryption and decryption. It is therefore critical that a secure method is considered to transfer the key between sender and recipient.
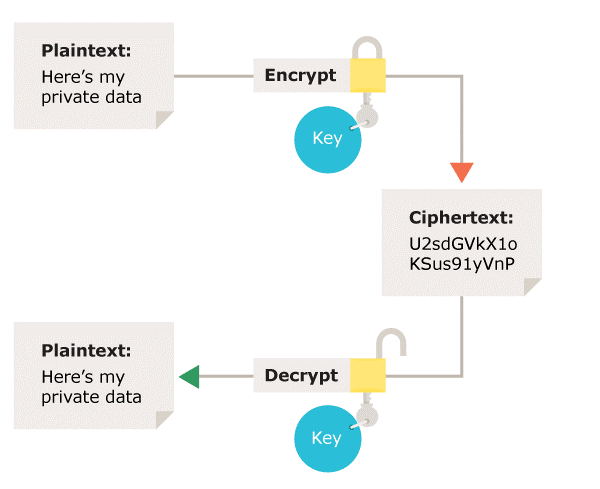 Figure 2: Symmetric encryption – Using the same key for encryption and decryption
Figure 2: Symmetric encryption – Using the same key for encryption and decryption
What is asymmetric encryption?
Asymmetric encryption uses the notion of a key pair: a different key is used for the encryption and decryption process. One of the keys is typically known as the private key and the other is known as the public key.
The private key is kept secret by the owner and the public key is either shared amongst authorised recipients or made available to the public at large.
Data encrypted with the recipient’s public key can only be decrypted with the corresponding private key. Data can therefore be transferred without the risk of unauthorised or unlawful access to the data.
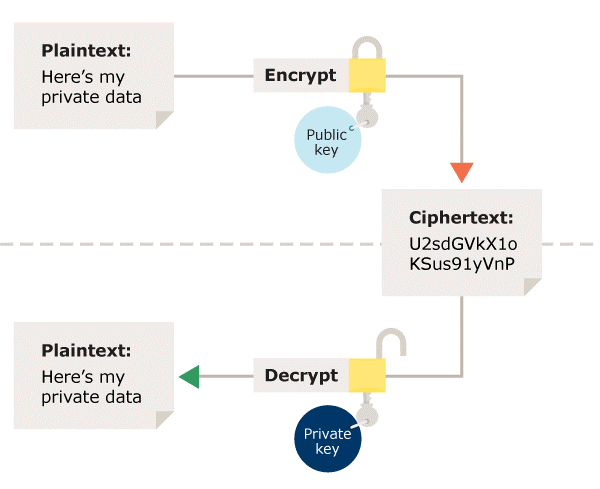
Figure 3: Asymmetric encryption – Using a different key for the encryption and decryption process
What about hashing?
Hashing is a technique that generates a fixed length value summarising a file or message contents. It is often incorrectly referred to as an encryption method.
Hash functions are used with cryptography to provide digital signatures and integrity controls but as no secret key is used it does not make the message private as the hash can be recreated.
Further reading